Problem Description
In normal case, users might secure all pages by
<intercept-url pattern="/**" access="ROLE_USER" />
In this case, we need to set login page for anonymous users.
According to http://docs.spring.io/spring-security/site/docs/3.2.5.RELEASE/reference/htmlsingle/#ns-form-and-basic (since spring security 3.1, it allows multiple <http>)
It is also possible to have all requests matching a particular pattern bypass the security filter chain completely, by defining a separate http element for the pattern like this:
<http pattern="/login.zul*" security="none"/>
But if we use it to bypass a zul page and zk secure event feature, it will cause 2 nested login window opened when you trigger a secured event with unauthorized role.
Steps to Reproduce
- run attached project
- visit loginIssue.zul
- click the button.
The Button's onClick event is secured by zk spring security
Actual Result
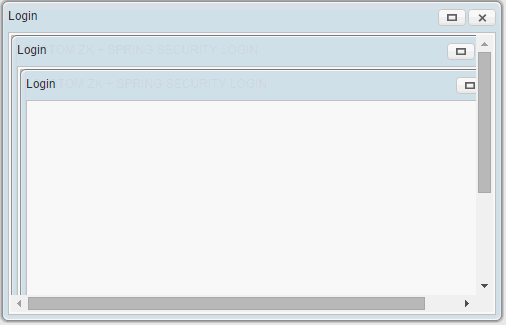
Alternative Solution
Use intercept-url in the same <http> instead of separate <http>, e.g.
<http auto-config="true"> <!-- alternative configuration that doesn't cause nested login window <intercept-url pattern="/login.zul" access="IS_AUTHENTICATED_ANONYMOUSLY" /> <intercept-url pattern="/main.zul" access="IS_AUTHENTICATED_ANONYMOUSLY" /> <intercept-url pattern="/**" access="ROLE_USER" /> </http>